Better Action Practices
Add permissions to every workflow
- By default, Actions might have R/W to everything in repo
- This is set in Settings > Actions at repo or org level
- Let’s ensure we start with a "least privilege" mindset in
wordsmith-web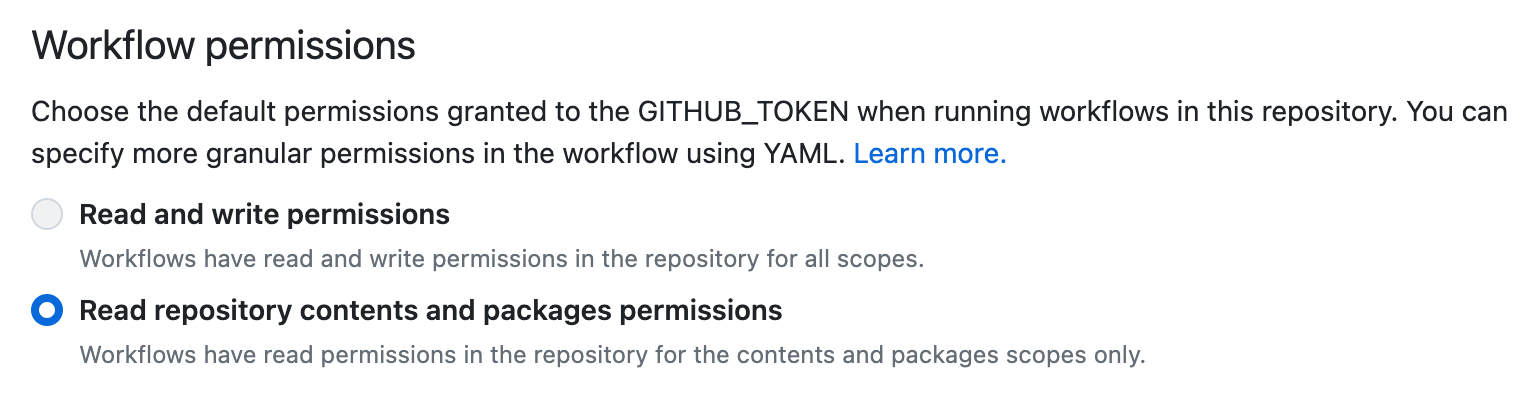
- Go to org Settings > Actions > General > Workflow Permissions
- Ensure it’s set to
Read repository contents and packages permissions - Manually add permissions needed to each workflow (next slide)
- Permissions can be per workflow or per job (see all perms)
Permission options for GITHUB_TOKEN
- Add the ones you need, it’ll set the rest to
none(docs) - You can do this at root or per-job level
permissions:
actions: read|write|none
checks: read|write|none
contents: read|write|none
deployments: read|write|none
id-token: read|write|none
issues: read|write|none
discussions: read|write|none
packages: read|write|none
pages: read|write|none
pull-requests: read|write|none
repository-projects: read|write|none
security-events: read|write|none
statuses: read|write|none- Sometimes you need none (when your workflow doesn’t need to access its repo)
permissions: {}